With the increasing number of web applications and modern technologies, online authentication and authorization have become crucial. JWT or JSON Web Token is a popular authentication method used by developers. JWT token comprises a header, a payload, and a signature that contains relevant user information. It is portable, secure, and scalable. In this blog, we’ll dive deeper into JWT tokens used in authentication and explore their benefits.
What is JWT Token?
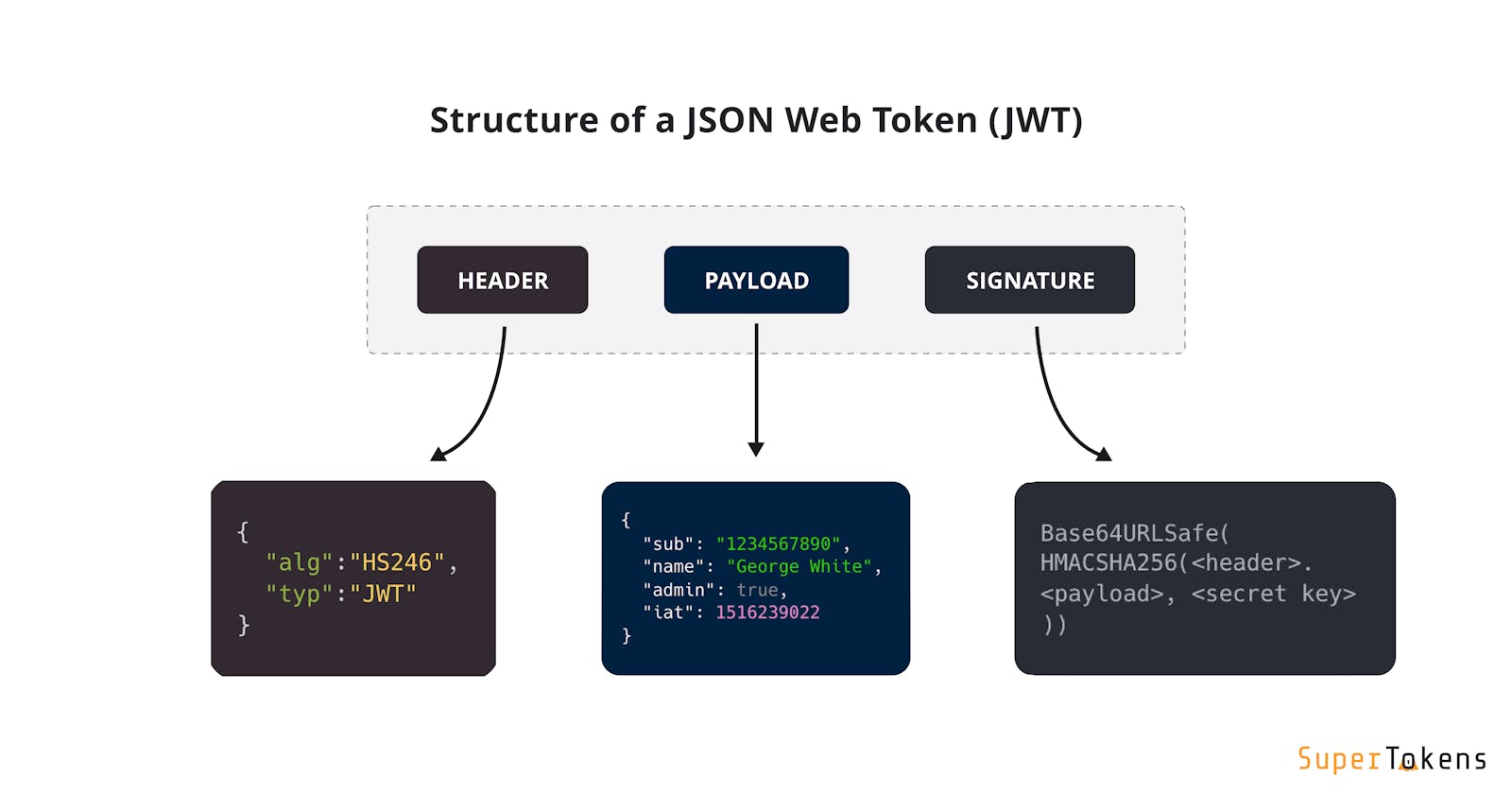
JWT token is an open-standard for transmitting data securely between two endpoints. It is formed by combining three parts: the header, the payload, and the signature.
Header: This contains metadata in JSON format about the token, including the algorithm used for signature and the token type.
Payload: This contains user information in JSON format that can be in the form of claims or attributes.
Signature: This is generated using the algorithm provided by the header and encoded with the payload information.
Once a user successfully logs in, the server generates a JWT token with the required user information, and the token is sent to the client-side. The client-side then sends this JWT token with every request it makes to the server, and the server verifies the authenticity of the token before providing access to the requested resource.
Benefits of JWT Token in Authentication
Stateless: JWT tokens are stateless, meaning the server doesn’t need to keep any record of the token’s user session. This reduces the storage space needed on the server and minimizes the cost of storage.
Secure: JWT tokens are encrypted using the signature method, which makes them more secure. The JWT token can’t be tampered with or altered, ensuring that the user’s information is safe.
Portable: Since JWT tokens don’t depend on any specific platform or programming language, they can be used across different languages and platforms, making them very flexible and portable.
Scalable: JWT tokens are an efficient way of handling user authentication since they can be shared between different servers, which makes them perfect for applications where different services are communicating with each other.
How to Implement JWT Token in Authentication
Install the required packages: The first step to implement JWT is to install the required packages in your application. The two most popular packages for this purpose are Passport JWT and JSON Web Token.
Create a JWT strategy: Create a strategy that will be used for authenticating the user’s JWT token. Passport JWT provides the JWT strategy that we’ll use here.
Generate and send JWT token: After the user successfully logs in, the server generates a JWT token with the necessary user information, which is then sent to the client-side.
Send the token with every request: Once the client-side receives the JWT token, it should include the token in the
Authorizationheader with every request it makes to the server.Verify the token: The server verifies the token’s authenticity before providing access to the requested resource. If the token is invalid, the server will return a 401 Unauthorized error.
Conclusion
JWT tokens are an efficient way of handling user authentication and authorization for web and mobile applications. They are portable, scalable, secure, and stateless. By understanding how to generate and use JWT tokens, you can improve the security and scalability of your applications.
Thank you for reading! If you have any questions or comments, please feel free to leave them below.